WHITEPAPERS
What Engineering Leaders Need To Know About IoT Security
Be prepared to make the necessary right trade-offs when securing your product or service without unduly compromising user experience, project timelines, or budget requirements.
Authors:
Jeff McGehee, Director of Engineering
Daniel Spofford, Director of Software Engineering
Mitchel Haan, Senior Software Engineer
IoT technology spurs incredible economic growth, and improves lives. Yet, there are substantial risks associated with the technology when it’s not properly secured. In this guide we present the most important principles and best practices that engineering leaders should be familiar with to minimize IoT security risks.
➜ What Is IoT Security?
➜ Why IoT Security Matters
➜ Defending Physical Devices
➜ Protecting Firmware and Software
➜ Ensuring IoT Network Security
➜ Storing and Consuming Data Safely
What Is IoT Security?
With billions of connected devices in operation globally and the total number continuing to grow rapidly, it is an exciting time for the Internet of Things (IoT). With a diverse set of applications in healthcare, manufacturing, and transportation, the IoT will continue to spur incredible economic growth while improving people’s quality of life across the globe.
Unfortunately, the situation is not entirely rosy; malign forces are using IoT technology for their own ends. For example, security researchers have demonstrated the feasibility of using vulnerabilities in IoT devices to deploy ransomware into organizational networks. Government-sponsored hackers have also deployed specially-designed malware in an attempt to shut down entire power grids.
In the face of this, engineering leaders need to understand the principles of IoT security to minimize the likelihood and severity of such attacks. At the same time, they need to get the job done on time and within budget.
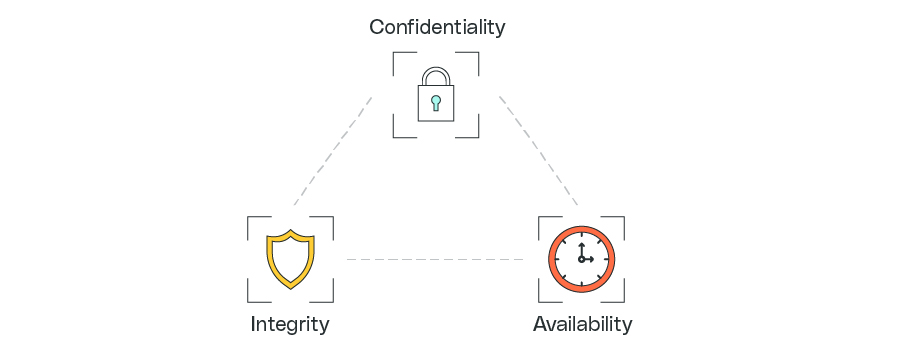
In short, IoT security is the practice of efficiently protecting the confidentiality, integrity, and availability of data processed by or stored in connected devices against malicious attacks. These attributes, known as the CIA triad, describe the aspects of data that you need to keep your business running and meet customer demands. Protecting them in a cost-effective manner should form the center of your security strategy.
Why IoT Security Matters
Managing Risk While Delivering Value
The broader discipline of cybersecurity is all about risk management, and this is absolutely true for IoT security as well. The internet and the businesses built on top of it deliver incredible value and allow people to live and work in ways that were previously unimaginable. At the same time, malicious actors have taken notice of this value generation and have deployed all manner of techniques to profit from it by stealing, corrupting, and destroying data.
We need only look at a few examples to understand how high the stakes are:
- As of mid-2022, the average amount paid to hackers to disable ransomware after a successful attack exceeded $100,000.
- State-sponsored cyber espionage incidents haved threatened national security and cost billions of dollars to contain and mitigate.
- Known vulnerabilities in medical devices have put human lives at risk.
These threats demand action, but exactly how to proceed isn’t always clear. As some security experts have said facetiously, “to secure a system well, we should power it down, encase it in concrete, and drop it to the bottom of the ocean.” Given the massive economic and humanitarian benefits delivered by technology, protecting a system in such a manner would be quite foolish.
Thus, we’re left with an uncomfortable tension between the enormous benefits of internet-connected products and services and the chance that attackers can use them to cause harm. The only way to proceed rationally in the face of this situation is to balance the risk of using a certain application or technology against the rewards to be had.
IoT Security Challenges
In the IoT world, understanding this balance is all the more important because of the inherently close interaction between the digital and physical domains. Miscalculation can quite conceivably lead to an injury or death; hackers of all stripes continue to target connected systems with lethal intent. A survey of recent incidents shows this all too clearly:
- In late 2017, the cybersecurity firm Mandiant published a report about what it called TRITON malware. The company detailed how this malware was “designed to manipulate industrial safety systems.” Mandiant also determined with “moderate confidence that the attacker was developing the capability to cause physical damage and inadvertently shutdown operations.”
- Two years later, security researchers developed an Android application demonstrating that it was possible to kill people by exploiting flaws in a widely used insulin pump.
- In two separate incidents in 2021, hackers attempted to poison public water supplies in California and Florida by manipulating purification systems.
In the face of such dangers, the importance of securing IoT deployments snaps into focus.
IoT Security Standards
Unfortunately, there is no single, unifying, industry-wide standard of security for IoT applications; a complex web of guidance, best practices, and regulation currently drives real-world implementations. For example:
- The non-profit IoT Security Foundation and the U.S. National Institute of Standards and Technology maintain helpful frameworks for securing networks of connected devices.
- The Open Web Application Security Project (OWASP) publishes a “top 10” list of common vulnerabilities in IoT deployments to educate practitioners regarding common security risks.
- The American federal government promulgated requirements for procurement of connected devices via the IoT Cybersecurity Improvement Act of 2020.
- The State of California (USA) wrote into law various IoT security practices via Senate Bill (SB) 327.
- The United Kingdom’s sweeping Product Security and Telecommunications Infrastructure Bill (PSTI) includes IoT-related provisions.
In light of these various suggestions and mandates, implementing an effective IoT security program demands discretion and experience. In the end, the requirements, challenges, and threats specific to your unique use case should ultimately drive your security-related decision-making. Making the optimal choices requires engineering leaders to weigh both a variety of potential risks and an array of options to manage them.
Balancing Competing Demands
Security initiatives always come with costs and require trade-offs, making it difficult for organizations to decide how to make them. No project can have an infinite budget, let alone for just security. Organizations need to be able to make calculated decisions about how to manage their risk, both from a cybersecurity and business perspective.
To do so, engineering leaders need to know two main things about IoT security:
- What should I look for in a partner’s IoT security solutions?
- How can I operate these solutions securely?
To evaluate these questions, we’ll follow the path of data from an individual device – where it is collected – to the end user who consumes it from what we will call a “hub.” Although clear hub-and-spoke models for IoT deployments are blurring with the emergence of “fog computing,” there is almost always some central repository of data and computation at the center of an IoT network. Your organization may manage it directly in an on-premises data center, use infrastructure-as-a-service (IaaS) or platform-as-a-service (PaaS) offerings hosted by a public cloud service, or a third party might manage the hub on your behalf through a software-as-a-service (SaaS) model. In any case, the security of this hub can be just as critical — and potentially more so — to your network’s security as that of individual devices.
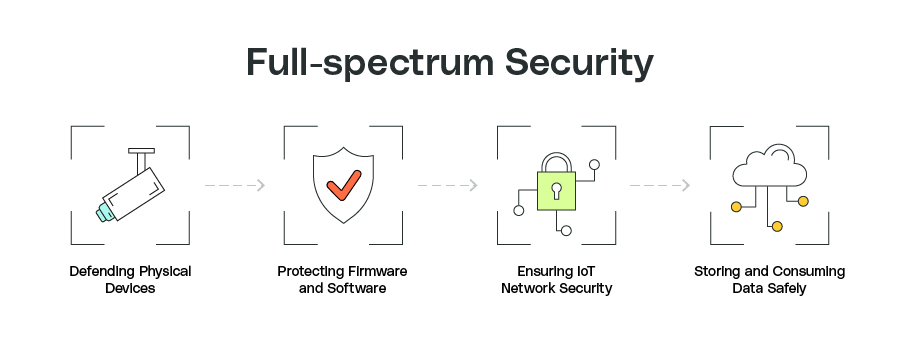
To illustrate the journey of data from device to hub, we’ll focus on four main security tasks:
1. Defending physical devices
2. Protecting firmware and software
3. Ensuring IoT network security
4. Storing and consuming data safely
Before diving in, though, it makes sense to review some general principles for IoT security that are applicable in every situation.
Use Threat Modeling To Enumerate Potential Attacks
No IoT deployment exists in a vacuum; the business purpose for developing it in the first place is critical to determining how to secure it. The sensitivity and financial value of the data you are handling, combined with the expertise and resources of those who might try to attack it, should drive your security decision-making. When you factor in the planned technical architecture of your system, you can establish a formal “threat model” to guide its design and development, as well as any trade-offs you might need to make along the way.
Per OWASP, “Threat modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.” Through such a structured mental exercise, you can understand the risks to your IoT deployment ahead of time, potentially mitigating many before they ever materialize.
The level of detail of your threat model can and should vary based on the complexity and value of your operations and the likely threats to them. If you’re building an IoT product that doesn’t handle sensitive data or interact with safety-critical processes, then something like the Mozilla Rapid Risk Assessment (RRA) might be an appropriate tool to rapidly analyze certain aspects of your system. On the other hand, if your IoT offering will be used in settings where maintaining the confidentiality of information is paramount, or there is the potential for it to interact with industrial control systems, a more in-depth process such as that suggested by OWASP or the Microsoft Security Development Lifecycle (SDL) threat modeling approach might be more appropriate.
In any case, deliberate security planning at the outset of your project can save you valuable time and resources while protecting your system and its users.
Let Your Use Case Be Your Guide
As part of your threat modeling process, it’s important to consider the implications of a cybersecurity incident and let that determine the amount of time and money you invest in securing your IoT devices. Nothing in the world exists merely to be secure, and you must meet customer demands while contending with resource limitations.
For example, if you are using simple beacons to do inventory tracking, the consequences of a hacker spoofing or impersonating a device may be small. Using a relatively simple and cheap type of device authentication — and accepting some cybersecurity risk — might well be appropriate for the situation. Conversely, if your IoT project involves highly sensitive information such as health data, or could conceivably have physical safety implications such as in a connected factory setting, your risk tolerance should be much lower.
Develop a Shared Security Model
Modern IoT deployments represent a web of interconnected technologies, protocols, and organizations. A different vendor might each be responsible for manufacturing your physical devices, programming their firmware, deploying analytics solutions to them, and storing the data they capture in the cloud. Oftentimes it isn’t clear exactly where one company’s responsibility for cybersecurity ends and where another’s begins. These gaps are often excellent targets for malicious actors.
To address such ambiguity, during the design phase of your IoT project you should develop a shared security model allocating responsibility to the various parties involved. This can include identifying who will physically secure your connected devices and how, who will provide firmware and software patches for them and when, and what person or organization can authorize and control access to the data your system collects. Whenever possible, establish these requirements contractually and conduct due diligence of the relevant parties to ensure they’re meeting their obligations.
With these principles established, let’s dive more deeply into the topic of IoT security, following data from its collection at the individual device level through its consumption by the end user.
Defending Physical Devices
IoT data must necessarily originate from a distributed network of physical machines. Although this web of physical sensors are what facilitate the incredible value that the IoT offers, they themselves can serve as cyber attack vectors, targets, or both.
So-called “air-gapped” deployments — separated from the public internet — can be infected with malware through poor device security, as once happened in a nuclear power plant. In this situation, removable USB drives were the likely culprit. Even more alarming is the prospect of counterfeit or malicious hardware being introduced into an enterprise network via a supply chain attack. In a simpler but no less concerning scenario, a relatively unsophisticated attacker could steal one of your devices and access the sensitive data on it, if insufficiently protected.
To defend against these threats, leaders need to understand the key considerations of device-level security, from both the perspective of evaluating a potential partner and that of operating the device on a daily basis.
What To Look for in a Partner’s IoT Security Solutions
Ensuring there is a secure foundation in place is a critical step toward protecting your IoT deployment. Due to the increasing volume and severity of attacks against technology supply chains, making sure that your devices aren’t compromised before they arrive on site is a key step. To prevent this from happening, ask your IoT partner the following questions:
- Do the devices use tamper-proof hardware?
- What supply chain integrity verification methods do you use?
- Have any of the devices ever had non-unique default passwords?
How To Operate Securely
Your security responsibilities don’t end once you’ve selected an IoT partner and acquired the necessary hardware and software. Those operating networks of connected devices have a responsibility to maintain and secure them on a continuing basis. To do so, your enterprise needs a comprehensive plan that allows it to:
- Limit physical access to your devices
- Not store or process unnecessary data on the device
- Only enable physical features necessary to get the job done
- Dispose of your devices in a safe manner
Protecting Firmware and Software

Another critical aspect of IoT security is the code running on your physical device. Both firmware — specialized code which interacts with the device’s electrical components — and software — responsible for processing and transmitting data — require protection against malicious attack.
Hackers can target firmware to embed code that compromises the device or your entire network. They have frequently targeted this aspect of IoT networks to cause damage by “bricking” devices; rendering them completely unusable by corrupting some aspect of the firmware.
- The VPNFilter malware could effectively render devices unusable by overwriting part of their firmware and then rebooting them.
- Similarly, attackers used Silex malware to completely disable thousands of IoT devices by overwriting their firmware.
If they’re able to infiltrate the device’s software, attackers can access higher-level computational functions to conduct more sophisticated attacks.
- The infamous denial-of-service attack on the domain name service provider Dyn involved hundreds of thousands of commandeered security cameras, wireless routers, and other internet-connected appliances. Assembling them into the “Mirai botnet,” a third party then used this army of zombie devices to launch its attack.
- Hackers have even “cryptojacked” IoT devices to steal processing power for mining cryptocurrency. These efforts are especially insidious due to the fact that, in addition to consuming additional electricity, cryptojacked devices might be unable to complete their designed task while under this additional strain.
Given these threats, securing the code running on your IoT devices is a critical aspect of any project. Both you and your partner organization have various responsibilities, which you should clarify upfront.
What To Look for in a Partner’s IoT Security Solutions
As with physical devices themselves, ensuring that your IoT partner has its act together at the application (i.e. firmware and software) layer is important. Unless you’re designing and building the entire technology stack that will run in your network, you will need to rely on others to do some of the key work for you in this respect. To make sure you are sufficiently protected, you should ask pointed questions about the following:
- How do you minimize the device’s digital risk surface?
- Are there any hard-coded secrets present on the devices?
- Will the system store any sensitive information in plain text?
- How do you prevent, identify, and remediate vulnerabilities?
- How does the solution facilitate firmware and software updates?
How To Operate Securely
Exactly who is responsible for which aspects of your IoT deployment’s firmware and software security should be clear from the shared security model you built at the outset of the project. As you bring your system online though, there are certain steps that you will most likely be responsible for to ensure it is running securely:
- Monitor running code for vulnerabilities and anomalies.
- Actually update vulnerable software and firmware.
- Have an incident response plan.
Ensuring IoT Network Security
Now that you have taken care of securing the digital and physical aspects of the devices themselves, you need to ensure that your data gets where it needs to go while preserving its CIA. While the previous two sections of this paper focused primarily on the security of “data at rest,” this part explores the security implications of “data in motion.”
Ensuring that this information is secure is a team effort between your organization and your IoT partner. Making sure both teams are clear on their responsibilities through a shared security model is vital for ensuring you have a comprehensive plan in place.
What To Look for in a Partner’s IoT Security Solutions
Unless you’re outsourcing the entire operation of your IoT deployment to a third party, managing the communications between devices and the central hub will most likely be your responsibility. With that said, how effectively and securely you’re able to do so will depend to a large extent on how the hardware and software components of your connected devices are designed. Thus, you should ask your partner:
- How are devices authenticated to the hub?
- How does the device communicate securely with the hub?
How To Operate Securely
As your enterprise will generally be responsible for the day-to-day operations of your deployment, securing it in a production situation will most likely fall to your team. Some key steps you can take toward this end are to:
- Implement a Zero Trust strategy.
- Verify, rotate, and manage your certificates.
Storing and Consuming Data Safely
Once data has left your IoT devices you can further analyze, process, and visualize it for human consumption, or send it to other systems in a machine-readable format. Additionally, organizations often store their IoT-derived data in centralized repositories, either in data centers they own and operate, in a customer-managed IaaS or PaaS offering hosted by a public cloud service, using a vendor-managed SaaS product, or some combination thereof.
At this stage, the physical location of and responsibilities for securing data often become fuzzy due to “cloud sprawl” and the complex interactions between various systems and organizations that take place as a result. Your shared security model becomes especially important at this juncture; it is a critical tool for shining light on what might otherwise be a confusing and potentially dangerous situation.
What To Look for in a Partner’s IoT Security Solutions
The modern technology landscape comprises a wide array of interconnected and interdependent software solutions of all kinds. Adding connected devices to the mix only makes things more complex. Since you’re almost always going to rely to some degree on a third party to secure your deployment, you should make sure that you understand the following from your IoT partner:
- What are your application security standards and practices?
- How do you facilitate my compliance with regulatory requirements?
How To Operate Securely
Regardless of which model you use for your hub — customer- or vendor-managed — your organizations will retain key responsibilities. To best protect your data against malicious attack, you should:
- Monitor for misconfigurations.
- Observe your environment in production.
Conclusion
Even if it were available, an unlimited security budget would never fully mitigate the risk of a malicious party impacting your IoT deployment. Due to the constrained resources every organization has to contend with, you must make tough, calculated decisions regarding where to implement security measures and where to accept risk.
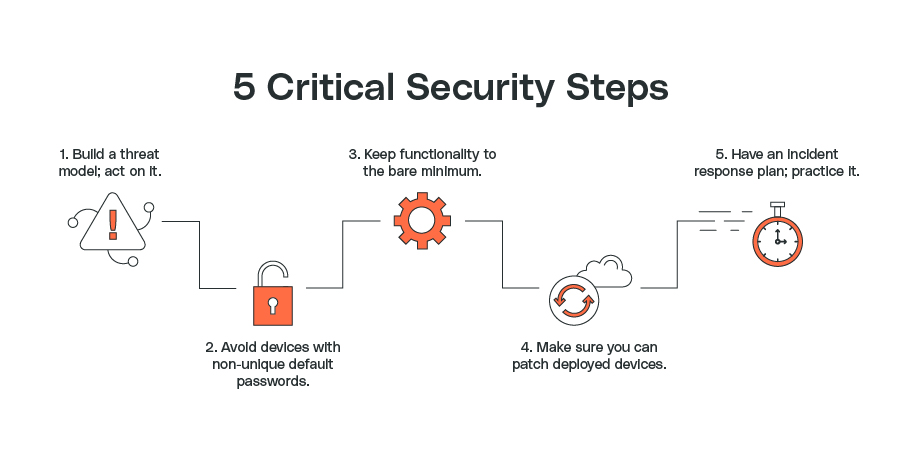
Those decisions don’t have to overwhelm your team or your budget, though. Building a series of small wins usually starts with connecting a few devices, absorbing some risk to test a select set of use cases, proving the model, and then growing your deployment into additional nodes and ultimately, fleets. Thus, if you are just beginning your security journey, start with the following five critical security steps:
- Build a threat model and act on it.
- Don’t buy devices that have ever had default non-unique passwords.
- Keep physical and digital functionality to the bare minimum required to achieve your business goals.
- Ensure you have a way to update and patch deployed devices.
- Develop and practice an incident response plan.
By following some or all of these recommendations to secure your devices, their firmware and software, their communications with your hub, and the final repository of your data, you can have greater confidence in the safety of your data — and your customers’ data — as you launch your IoT project. Additionally, you’ll be prepared to make the necessary right trade-offs when securing your product or service without unduly compromising user experience, project timelines, or budget requirements.